Why don't we settle the original question by
actual testing?
1. Clean install of 21H2 RTM.
2. Run
install_wim_tweak.exe, or another tool to unhide Windows packages.
Code:
dism /online /get-packages | findstr /i defender
Package Identity : Windows-Defender-AM-Default-Definitions-Package~31bf3856ad364e35~amd64~en-US~10.0.19041.1
Package Identity : Windows-Defender-AM-Default-Definitions-Package~31bf3856ad364e35~amd64~~10.0.19041.1
Package Identity : Windows-Defender-AppLayer-Group-Package~31bf3856ad364e35~amd64~en-US~10.0.19041.662
Package Identity : Windows-Defender-AppLayer-Group-Package~31bf3856ad364e35~amd64~~10.0.19041.746
Package Identity : Windows-Defender-ApplicationGuard-Inbox-Package~31bf3856ad364e35~amd64~en-US~10.0.19041.1
Package Identity : Windows-Defender-ApplicationGuard-Inbox-Package~31bf3856ad364e35~amd64~~10.0.19041.844
Package Identity : Windows-Defender-ApplicationGuard-Inbox-WOW64-Package~31bf3856ad364e35~amd64~en-US~10.0.19041.1
Package Identity : Windows-Defender-ApplicationGuard-Inbox-WOW64-Package~31bf3856ad364e35~amd64~~10.0.19041.746
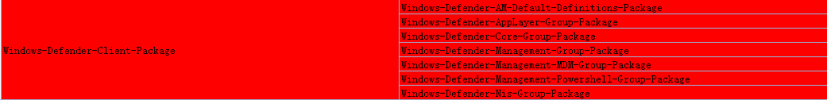
Package Identity : Windows-Defender-Client-Package~31bf3856ad364e35~amd64~en-US~10.0.19041.964
Package Identity : Windows-Defender-Client-Package~31bf3856ad364e35~amd64~~10.0.19041.1202
Package Identity : Windows-Defender-Core-Group-Package~31bf3856ad364e35~amd64~en-US~10.0.19041.964
Package Identity : Windows-Defender-Core-Group-Package~31bf3856ad364e35~amd64~~10.0.19041.1202
Package Identity : Windows-Defender-Group-Policy-Package~31bf3856ad364e35~amd64~en-US~10.0.19041.1023
Package Identity : Windows-Defender-Group-Policy-Package~31bf3856ad364e35~amd64~~10.0.19041.1023
Package Identity : Windows-Defender-Management-Group-Package~31bf3856ad364e35~amd64~en-US~10.0.19041.1
Package Identity : Windows-Defender-Management-Group-Package~31bf3856ad364e35~amd64~~10.0.19041.746
Package Identity : Windows-Defender-Management-MDM-Group-Package~31bf3856ad364e35~amd64~en-US~10.0.19041.1
Package Identity : Windows-Defender-Management-MDM-Group-Package~31bf3856ad364e35~amd64~~10.0.19041.1
Package Identity : Windows-Defender-Management-Powershell-Group-Package~31bf3856ad364e35~amd64~en-US~10.0.19041.1
Package Identity : Windows-Defender-Management-Powershell-Group-Package~31bf3856ad364e35~amd64~~10.0.19041.1
Package Identity : Windows-Defender-Nis-Group-Package~31bf3856ad364e35~amd64~en-US~10.0.19041.1
Package Identity : Windows-Defender-Nis-Group-Package~31bf3856ad364e35~amd64~~10.0.19041.1
3. Remove the obvious first choices:
Group Policy, MDM Group and
Powershell modules.
Code:
dism /online /remove-package /packagename:Windows-Defender-Group-Policy-Package~31bf3856ad364e35~amd64~en-US~10.0.19041.1023 /packagename:Windows-Defender-Group-Policy-Package~31bf3856ad364e35~amd64~~10.0.19041.1023 /packagename:Windows-Defender-Management-MDM-Group-Package~31bf3856ad364e35~amd64~en-US~10.0.19041.1 /packagename:Windows-Defender-Management-MDM-Group-Package~31bf3856ad364e35~amd64~~10.0.19041.1 /packagename:Windows-Defender-Management-Powershell-Group-Package~31bf3856ad364e35~amd64~en-US~10.0.19041.1 /packagename:Windows-Defender-Management-Powershell-Group-Package~31bf3856ad364e35~amd64~~10.0.19041.1
My Start Menu stopped working after removals, so I rebooted.
4. Remove ApplicationGuard or WDAG.
Code:
Windows-Defender-ApplicationGuard-Inbox-Package~31bf3856ad364e35~amd64~en-US~10.0.19041.1
Windows-Defender-ApplicationGuard-Inbox-Package~31bf3856ad364e35~amd64~~10.0.19041.844
Windows-Defender-ApplicationGuard-Inbox-WOW64-Package~31bf3856ad364e35~amd64~en-US~10.0.19041.1
Windows-Defender-ApplicationGuard-Inbox-WOW64-Package~31bf3856ad364e35~amd64~~10.0.19041.746
5. Remove Defender AV definitions.
Code:
Windows-Defender-AM-Default-Definitions-Package~31bf3856ad364e35~amd64~en-US~10.0.19041.1
Windows-Defender-AM-Default-Definitions-Package~31bf3856ad364e35~amd64~~10.0.19041.
Reboot required.
6. Remove Defender-Core. DISM isn't allowed, unless I disable Tamper Protection
Code:
Windows-Defender-Core-Group-Package~31bf3856ad364e35~amd64~en-US~10.0.19041.964
Windows-Defender-Core-Group-Package~31bf3856ad364e35~amd64~~10.0.19041.1202
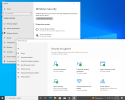
Reboot required. That's the real Defender Platform, and removing it hides the Virus protection panel.
7. Remove Defender-NIS (Network Inspection Service).
Code:
Windows-Defender-Nis-Group-Package~31bf3856ad364e35~amd64~en-US~10.0.19041.1
Windows-Defender-Nis-Group-Package~31bf3856ad364e35~amd64~~10.0.19041.1
8. Remove Defender-AppLayer.
Code:
Windows-Defender-AppLayer-Group-Package~31bf3856ad364e35~amd64~en-US~10.0.19041.662
Windows-Defender-AppLayer-Group-Package~31bf3856ad364e35~amd64~~10.0.19041.746
Not sure what that disabled.
9. Remove Defender-Client.
Code:
Windows-Defender-Client-Package~31bf3856ad364e35~amd64~en-US~10.0.19041.964
Windows-Defender-Client-Package~31bf3856ad364e35~amd64~~10.0.19041.1202
Not sure what that disabled.
10. Conclusion:
Removing the Defender feature packages removes Defender from the Security Center, while keeping non-Defender features (firewall, VBS isolation, application security) visible. If NTLite isn't separating the packages this way, then it should.
The one glitch is Protection areas doesn't hide "Virus & threat protection".