steven4554
New Member
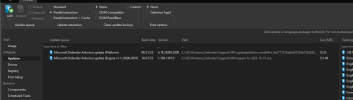
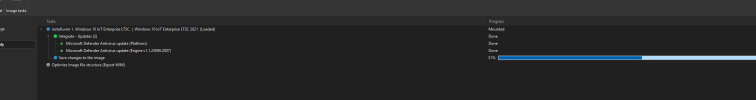
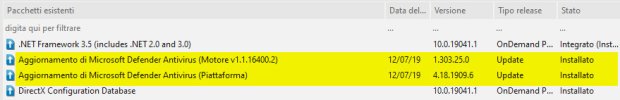
Include the ability to integrate the defender-dism-x64.cab into both Windows 10 and 11. I make these cabs and provide for download every Tuesday on MDL Forum and MSFN, so members can integrate them into their offline images. These cabs cannot be installed on a live OS, only offline images. I also make arm64 and x86 versions too.