VBScript deprecation: Timelines and next steps | Windows IT Pro Blog
Learn about the deprecation of Visual Basic Scripting edition.
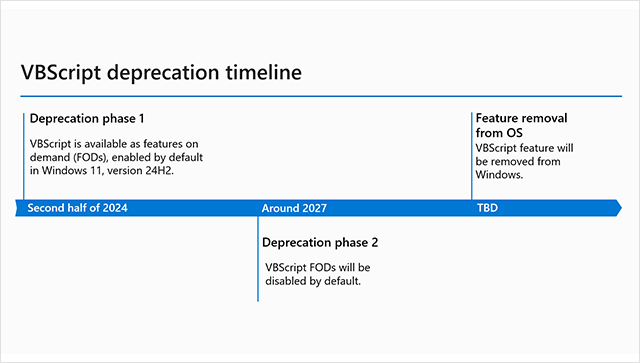
1. W11 24H2 will be the last release that enables VBScript to run by default.
2. Afterwards in 2027, you will have to manually enable it as a Feature on Demand.
3. Disappears completely from Windows in the W12 timeline.
Undoubtedly, some of you depend on the "invisible" VBS trick for hiding running CMD or PS scripts. No word yet if MS will provide an alternative method. The last time I checked PowerShell's open bugs, the PS team was pointing fingers at CMD/Terminal team ("hey, the visible window is a problem with their code").
